Data Loss Prevention (DLP) Implementation: Safeguarding Sensitive Data with Microsoft Purview
Estimated reading time: 8 minutes
Key Takeaways
- Data Loss Prevention (DLP) is essential for protecting confidential data from both internal and external threats.
- Microsoft Purview offers a unified platform for DLP policies, compliance, and data classification.
- Effective DLP policies minimize data breaches and aid in regulatory compliance.
- Accurate classification is key to applying the right controls to the right data.
- DLP must be part of a holistic information protection strategy, including encryption and access controls.
Table of contents
- Data Loss Prevention (DLP) Implementation: Safeguarding Sensitive Data with Microsoft Purview
- Key Takeaways
- Understanding Data Loss Prevention (DLP)
- Microsoft Purview: A Comprehensive DLP Solution
- Developing Effective DLP Policies
- Sensitive Data Classification
- Compliance Management Through DLP
- Information Protection Strategies
- Challenges and Solutions in DLP Implementation
- Conclusion
- Call to Action
- Frequently Asked Questions
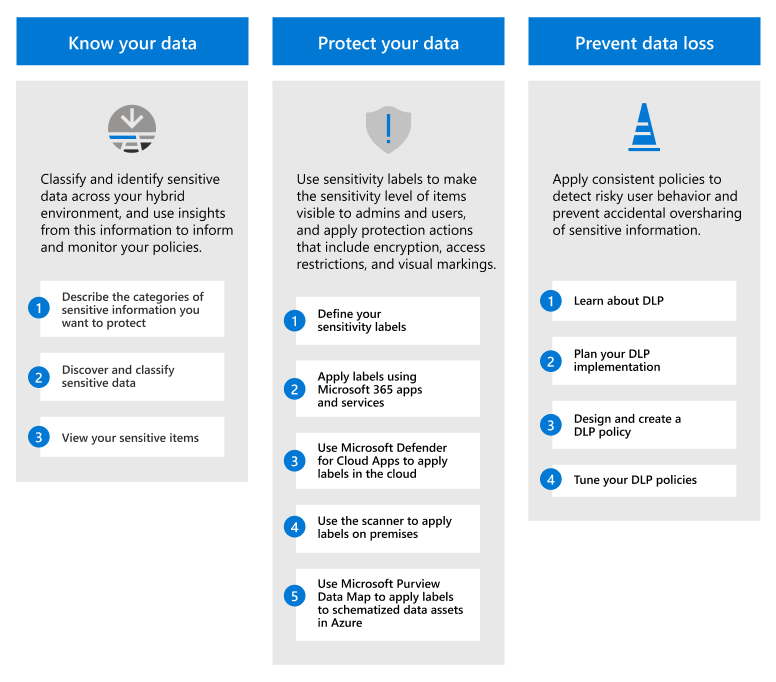
Understanding Data Loss Prevention (DLP)
Data Loss Prevention refers to the technologies and processes specifically designed to identify, monitor, and protect sensitive data from unauthorized access or leakage. These solutions act as guardians of your organization’s most valuable information assets.
The benefits of implementing DLP are substantial:
- Protection of confidential data against both internal and external threats
- Significantly reduced risk of potentially costly data breaches
- Stronger alignment with regulatory compliance requirements
- Enhanced visibility into how sensitive data flows within your organization
DLP serves as a cornerstone of information protection within a broader cybersecurity strategy. By implementing these technologies, organizations can maintain control over sensitive data regardless of where it resides or how it’s being used.
According to Microsoft, effective DLP can help organizations mitigate reputational damage and avoid substantial regulatory fines that often follow data breaches. This preventative approach proves far more cost-effective than dealing with the aftermath of a security incident.
Microsoft Purview: A Comprehensive DLP Solution
Microsoft Purview stands out as a unified platform for Data Loss Prevention implementation that brings together previously disparate security controls. This comprehensive solution centralizes policy management across your entire digital estate, offering built-in sensitive data classification capabilities that can identify and protect information based on content rather than just location.
A key strength of Purview is its seamless integration with the Microsoft 365 ecosystem, allowing for consistent protection policies across applications like SharePoint, Exchange, Teams, and OneDrive. This integration eliminates protection gaps that often occur with standalone solutions.
Microsoft Purview’s monitoring capabilities extend to data in all states:
- Data in use (being actively accessed by users)
- Data in motion (being transferred across networks)
- Data at rest (stored in databases, file shares, or cloud services)
This comprehensive visibility ensures no sensitive information escapes protection regardless of its state or location.
Beyond technical protections, Purview significantly supports compliance management through its extensive template library covering major regulations like GDPR, HIPAA, and PCI DSS. These ready-to-use templates and automated controls dramatically simplify meeting complex regulatory requirements (Essential 8 compliance implementation: a complete guide to building a resilient cybersecurity framework).
“Microsoft Purview offers a comprehensive platform for DLP implementation” across an organization’s entire digital estate, providing the tools needed to discover, classify, and protect sensitive information wherever it exists.
The platform’s integration capabilities allow it to work alongside other security measures, creating a defense-in-depth approach to information protection that addresses multiple threat vectors simultaneously.
Developing Effective DLP Policies
DLP policies form the backbone of any successful Data Loss Prevention implementation. These policies are essentially sets of rules that govern how sensitive data should be handled, stored, and shared throughout your organization. Without robust policies, even the most sophisticated DLP technology cannot effectively protect your information assets.
Creating and implementing effective DLP policies within Microsoft Purview involves several critical steps:
1. Identify Sensitive Data Types
Start by cataloging the types of sensitive data your organization handles, including:
- Financial records and account information
- Personally Identifiable Information (PII)
- Protected health information
- Intellectual property
- Confidential business documents
2. Define Clear Handling Rules
Establish specific rules for each data type, determining:
- Who can access specific categories of sensitive data
- What actions users can take with protected information
- Which data can be shared externally and under what conditions
- How data should be labeled and classified
3. Test Before Full Enforcement
Always deploy new policies in simulation mode first:
- Monitor policy matches without blocking legitimate activities
- Gather data on false positives and user impact
- Make necessary adjustments to reduce business disruption
4. Schedule Regular Reviews
Implement a policy maintenance schedule:
- Review effectiveness quarterly
- Update rules to address emerging threats
- Adjust to changing business requirements
- Incorporate feedback from end users
By following this structured approach, organizations can develop DLP policies that balance security requirements with business productivity needs. Remember that overly restrictive policies may drive users to seek workarounds, potentially creating new security gaps.
“Creating robust DLP policies is essential for protecting sensitive data” and should be approached as an ongoing process rather than a one-time implementation.
Sensitive Data Classification
Sensitive data classification serves as the foundation of effective Data Loss Prevention. This critical process identifies and tags information based on sensitivity level and risk, ensuring that appropriate DLP policies can be applied to each data category.
Without accurate classification, organizations risk either over-protecting non-sensitive data (creating workflow bottlenecks) or under-protecting truly sensitive information (leaving it vulnerable to exposure).
Microsoft Purview excels in this area through its sophisticated classification capabilities:
- Built-in sensitive information types that can identify common data patterns like credit card numbers, social security numbers, and health records
- Machine learning-based trainable classifiers that can recognize organization-specific document types and content patterns
To maximize the effectiveness of sensitive data classification, consider these practical tips:
Conduct a Thorough Data Inventory
- Map where sensitive data exists across your digital environment (hybrid cloud migration strategy)
- Identify both structured data (databases) and unstructured data (documents, emails)
- Determine how sensitive information typically flows through your organization
Leverage Multiple Classification Methods
- Start with Microsoft Purview’s pre-built classifiers for common data types
- Create custom classifiers for industry-specific or unique organizational data
- Use keyword dictionaries and regular expressions for specialized detection needs
- Implement exact data matching for precise identification of specific data sets
Build a Classification Taxonomy
- Develop a clear hierarchy of sensitivity levels (Public, Internal, Confidential, Restricted)
- Define specific handling requirements for each level
- Ensure classifications align with compliance requirements
“Accurate data classification enhances DLP effectiveness” by ensuring the right protection measures are applied to the right data, minimizing both security gaps and unnecessary restrictions on information flow.
Microsoft DLP overview provides deeper insights into classification best practices.
Compliance Management Through DLP
In today’s complex regulatory environment, compliance management has become a major challenge for organizations across industries. Key regulations like GDPR, HIPAA, CCPA, and PCI DSS impose strict requirements on how sensitive data must be protected, with significant penalties for non-compliance.
Data Loss Prevention plays a crucial role in meeting these obligations by providing the technical controls needed to enforce compliance policies. Microsoft Purview transforms this potentially overwhelming task into a manageable process through several key capabilities:
Pre-configured Compliance Templates
- Ready-to-use policy templates mapped directly to specific regulations
- Built-in sensitive information types aligned with compliance requirements
- Policy sets that address multiple regulatory frameworks simultaneously
Automated Discovery and Reporting
- Continuous scanning to identify regulated data across your environment
- Automated classification of content subject to regulatory protection
- Comprehensive dashboards showing compliance status and potential issues
- Detailed reports that can be shared with auditors and regulators
Robust Audit Capabilities
- Complete audit logs documenting policy matches and enforcement actions
- Evidence collection for demonstrating compliance efforts
- Incident investigation tools for addressing potential violations
- Historical records to satisfy regulatory retention requirements
By implementing Microsoft Purview’s compliance features, organizations can significantly reduce the manual effort required to maintain regulatory alignment while creating a defensible compliance posture.
“DLP plays a crucial role in regulatory compliance” by providing both preventive controls that stop violations before they occur and detective controls that identify issues requiring remediation.
Information Protection Strategies
While Data Loss Prevention forms a critical component of data security, effective information protection requires a holistic approach that addresses multiple aspects of security. Organizations should implement a comprehensive strategy that extends beyond DLP to create multiple layers of defense.
Key components of a complete information protection strategy include:
Encryption and Data Security
- Implement encryption for sensitive data both at rest and in transit
- Deploy rights management solutions to maintain control of documents outside your network
- Utilize secure deletion practices for data that has reached the end of its lifecycle
Access Controls and Authentication
- Implement strict access control lists (ACLs) based on least privilege principles (endpoint security)
- Require multi-factor authentication for accessing sensitive resources
- Regularly review and audit user permissions to prevent privilege creep
Employee Awareness and Training
- Develop clear data handling guidelines for all staff
- Conduct regular security awareness training focused on data protection
- Create a security culture that values and reinforces responsible data practices
Insider Risk Management
- Deploy tools to detect abnormal data access patterns
- Monitor for potential data exfiltration attempts
- Implement graduated response procedures for potential insider threats
Microsoft Purview enhances these strategies through its integration capabilities. The platform connects with:
- Microsoft Defender for comprehensive threat protection
- Azure Active Directory for identity and access management
- Microsoft Information Protection for document-level encryption
- Communication compliance tools to monitor for inappropriate sharing (Azure Virtual Desktop deployment)
This integrated approach creates a security ecosystem where different protections work together to safeguard sensitive information throughout its lifecycle.
The importance of combining DLP with encryption and access controls cannot be overstated. Each security layer addresses different aspects of protection, creating a defense-in-depth strategy that significantly reduces the risk of data exposure.
Learn more about these strategies in Microsoft Purview Data Loss Prevention documentation.
Challenges and Solutions in DLP Implementation
Despite its clear benefits, implementing Data Loss Prevention is not without challenges. Organizations frequently encounter several common hurdles that can impact the effectiveness of their DLP programs.
Challenge: False Positives
One of the most persistent issues with DLP technologies is false positive detections that trigger unnecessary alerts or block legitimate activities.
Solutions:
- Fine-tune detection rules with appropriate confidence thresholds
- Implement exception handling for approved business processes
- Regularly review alert patterns to identify and adjust problematic rules
- Leverage machine learning classifiers that improve accuracy over time
Challenge: User Resistance
Employees often perceive DLP controls as obstacles to productivity or signs of mistrust, leading to resistance or attempts to circumvent protections.
Solutions:
- Clearly communicate the purpose and importance of DLP to all stakeholders
- Provide transparent explanations when content is blocked
- Offer simple override procedures for legitimate business needs
- Gather and incorporate user feedback when refining policies
Challenge: Evolving Threats
The threat landscape constantly changes, with new data exfiltration techniques emerging regularly.
Solutions:
- Schedule quarterly policy reviews to assess effectiveness
- Subscribe to threat intelligence services for awareness of new risks
- Implement anomaly detection alongside rule-based protection
- Create a cross-functional team responsible for DLP policy maintenance
Challenge: Complex Environments
Many organizations struggle with implementing consistent DLP across diverse systems, platforms, and data repositories.
Solutions:
- Start with Microsoft Purview’s unified management approach
- Prioritize protection for the most sensitive data categories first
- Implement DLP in phases rather than attempting complete coverage immediately
- Integrate cloud and on-premises protections through hybrid configurations
By acknowledging these challenges and implementing the recommended solutions, organizations can significantly increase their chances of DLP success. Remember that DLP implementation is an ongoing process that requires continuous attention and refinement.
“Keeping policies updated with evolving threats” remains vital for maintaining effective protection against both current and emerging risks to sensitive data (cloud cost optimization strategies).
Learn more at Microsoft Purview DLP insights.
Conclusion
Data Loss Prevention (DLP) implementation represents a critical investment in your organization’s security posture and business continuity. Throughout this article, we’ve explored how robust DLP policies, accurate data classification, and integration with Microsoft Purview can significantly reduce the likelihood of costly and damaging data breaches.
The multi-faceted approach to data protection we’ve discussed addresses the complete lifecycle of sensitive information:
- Discovering where sensitive data exists across your environment
- Classifying that data according to sensitivity and regulatory requirements
- Protecting information through appropriate controls and restrictions
- Monitoring for potential policy violations and security incidents
- Responding effectively when issues are identified
Effective compliance management through DLP implementation helps organizations not only meet regulatory requirements but also demonstrate due diligence in protecting sensitive information. This proactive stance can significantly reduce both legal exposure and potential penalties.
Comprehensive information protection measures that combine DLP with complementary security controls create a defense-in-depth approach that addresses multiple threat vectors. This layered security strategy substantially increases the difficulty for both external attackers and potential insider threats to access sensitive data.
As data continues to grow in both volume and value, the importance of implementing strong DLP controls will only increase. Organizations that prioritize this aspect of security now will be better positioned to protect their critical information assets against evolving threats.
Call to Action
Now is the time to evaluate your organization’s current DLP readiness and data handling practices. Start by asking these essential questions:
- Do you know where your sensitive data resides across your digital estate?
- Have you classified your data according to sensitivity and regulatory requirements?
- Are appropriate controls in place to prevent unauthorized access or sharing?
- Can you demonstrate compliance with relevant data protection regulations?
If you’re uncertain about any of these areas, consider consulting with Microsoft partners or security experts who specialize in Data Loss Prevention (DLP) implementation. These professionals can provide tailored guidance based on your specific industry, compliance requirements, and security posture.
Take advantage of Microsoft’s resources for implementing Purview DLP:
- Request a demo to see the platform’s capabilities firsthand
- Participate in Microsoft Purview workshops to build implementation skills
- Engage with the Microsoft DLP community to learn from peers
- Consider a pilot implementation to assess impact and effectiveness
Remember that effective DLP policies require ongoing maintenance and refinement. Plan for regular reviews and updates to ensure your protection measures keep pace with both evolving threats and changing business needs.
By taking action today, you can significantly strengthen your organization’s data protection posture and reduce the risk of costly breaches, compliance violations, and reputational damage.
Frequently Asked Questions
- How does DLP differ from traditional security solutions?
- Is Microsoft Purview suitable for small and medium-sized businesses?
- Which regulations can be addressed using Microsoft Purview’s compliance templates?
- How often should DLP policies be reviewed?
- Do I need additional tools besides DLP to protect my data?
