Essential 8 Compliance Implementation: A Comprehensive Guide to Structured Cybersecurity
Estimated reading time: 12 minutes
Key Takeaways
- Essential 8 compliance is a baseline set of strategies designed to significantly reduce cyber risks.
- This framework provides a structured, step-by-step approach to cybersecurity.
- Australian organizations across various sectors benefit from applying these controls.
- Successful implementation requires regular patching, administrative privilege restriction, multi-factor authentication, and robust backups.
- Security audits and vulnerability management are crucial for maintaining and verifying compliance.
Table of contents
- Essential 8 Compliance Implementation: A Comprehensive Guide to Structured Cybersecurity
- Key Takeaways
- Understanding the Essential 8 Guidelines
- Cybersecurity Compliance in the Australian Context
- Implementing Essential 8 Compliance
- Integrating Security Audits into Compliance
- Vulnerability Management as a Core Component
- Achieving Structured Cybersecurity Compliance
- Conclusion
- Additional Resources
- Frequently Asked Questions
In today’s digital landscape, cybersecurity threats are evolving at an unprecedented rate. Organizations of all sizes face increasing risks, making Essential 8 compliance implementation a critical priority for business continuity and data protection. This comprehensive guide will walk you through implementing the Essential 8 framework to achieve robust cybersecurity compliance and protect your organization against the most common cyber attacks.
As cyber threats become more sophisticated, a structured approach to cybersecurity is no longer optional—it’s essential. The Essential 8 framework, developed by the Australian Cyber Security Centre, provides businesses with clear, actionable strategies to strengthen their security posture and meet Australian cybersecurity standards.
Understanding the Essential 8 Guidelines
The Essential 8 guidelines represent a baseline of cybersecurity controls designed to protect organizations from the majority of cyber threats. Developed by the Australian Cyber Security Centre (ACSC), these eight mitigation strategies help businesses prevent malware delivery and execution, limit the impact of security incidents, and recover data after a breach.
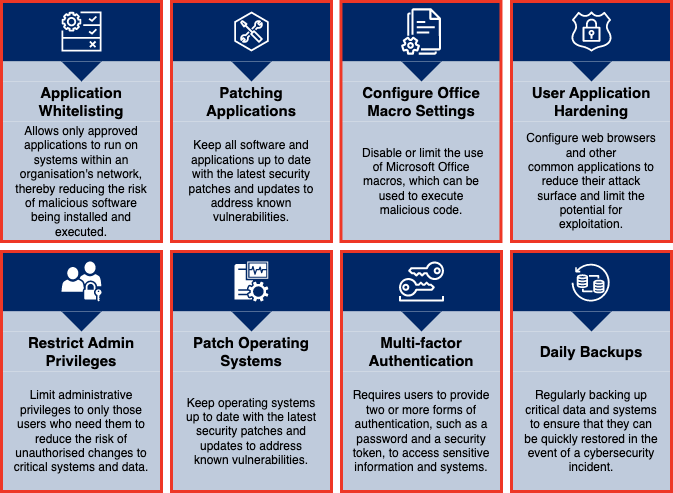
The eight strategies include:
- Application Control – Preventing execution of unapproved/malicious programs
- Patch Applications – Fixing security vulnerabilities in applications
- Configure Microsoft Office Macro Settings – Blocking macros from the internet
- User Application Hardening – Configuring web browsers to block Flash, ads, and Java
- Restrict Administrative Privileges – Limiting who can make system-wide changes
- Patch Operating Systems – Fixing security vulnerabilities in operating systems
- Multi-factor Authentication – Requiring multiple verification methods
- Regular Backups – Creating and testing secure data backups
These strategies work together to create a comprehensive security framework that significantly improves an organization’s cyber resilience. According to research, implementing these controls can prevent up to 85% of targeted cyber attacks. These strategies significantly improve cyber resilience by addressing the most common attack vectors used by cybercriminals. When implemented correctly, they form a powerful defense system against various security threats that organizations face daily. For more insights, refer to the UpGuard resource.
Cybersecurity Compliance in the Australian Context
Australian cybersecurity standards have evolved significantly in recent years, with the Essential 8 framework becoming a cornerstone of the national cybersecurity strategy. While initially developed for government agencies, these guidelines are now widely recognized as best practice for organizations across all sectors.
For Australian businesses, understanding the regulatory landscape is crucial. The Essential 8 guidelines align with broader compliance requirements and provide a structured approach to meeting security obligations. Although compliance with the Essential 8 is not legally mandated for all organizations, it’s strongly recommended and increasingly expected by customers, partners, and stakeholders.
Government agencies and critical infrastructure providers face stricter requirements, with many required to implement the Essential 8 as a minimum baseline for cybersecurity protection. For these organizations, compliance is not optional but a regulatory necessity.
According to security experts, the Essential 8 framework represents a scalable approach that organizations can implement progressively, starting with the most critical systems and gradually expanding protection across their entire infrastructure. This staged implementation helps organizations balance security needs with operational requirements. This is particularly important when considering strategies like Hybrid Cloud Migration, which integrate on-premises and cloud infrastructures.
Essential 8 is a recommended baseline for various government agencies and is increasingly being adopted across private sectors as well, particularly in finance, healthcare, and critical infrastructure. Learn more from this Scytale guide.
Implementing Essential 8 Compliance
Successful Essential 8 compliance implementation requires a systematic approach. Here’s a detailed, step-by-step guide to help you navigate this process effectively:
1. Assess Your Current Security Posture
- Identify systems and data requiring protection
- Document existing security measures
- Determine gaps between current state and Essential 8 requirements
- Prioritize areas needing immediate attention
2. Implement Application Control
Application control prevents unauthorized applications from running on your systems:
- Deploy whitelisting solutions like Microsoft AppLocker or similar tools (Infrastructure as Code with Terraform)
- Create rules allowing only approved applications to execute
- Test thoroughly before full deployment
- Establish processes for reviewing and approving new applications
3. Patch Applications Regularly
Unpatched applications are a common entry point for attackers:
- Create an inventory of all applications
- Establish a regular patching schedule (at least monthly)
- Prioritize security-critical applications
- Test patches before deploying to production
- Implement automated patch management where possible
4. Configure Microsoft Office Macro Settings
Malicious macros are a common attack vector:
- Block macros from the internet
- Only allow macros from trusted locations
- Configure macro settings via Group Policy
- Train users on the risks of enabling unknown macros
5. Apply User Application Hardening
Harden user applications to minimize attack surface:
- Configure web browsers to block Flash content and ads
- Disable unnecessary browser plugins and extensions
- Prevent users from changing security settings
- Implement content filters and web protection
6. Restrict Administrative Privileges
Limit administrative access to reduce potential damage:
- Audit and document all accounts with administrative privileges
- Remove unnecessary admin rights (Azure Virtual Desktop Deployment)
- Implement just-in-time privileged access
- Require approval for administrative actions
- Review privileged accounts regularly
7. Patch Operating Systems
Keep operating systems current with security updates:
- Establish automated OS patching processes
- Test patches thoroughly before deployment
- Prioritize critical security updates
- Create emergency patching procedures for zero-day vulnerabilities
8. Deploy Multi-factor Authentication (MFA)
MFA adds an essential layer of security:
- Implement MFA for all remote access
- Require MFA for privileged account actions
- Consider MFA for all users, not just administrators
- Select appropriate authentication methods (SMS, app-based tokens, hardware tokens)
9. Arrange Regular Backups
Effective backup strategies enable recovery after incidents:
- Back up all critical data regularly
- Store at least one backup copy offline (Cloud Cost Optimization)
- Test backup restoration processes
- Document recovery procedures
- Implement encryption for backup data
Remember that achieving cybersecurity compliance is not a one-time project but an ongoing process requiring continuous monitoring, adjustment, and improvement. Start with the highest-priority areas that provide the most security benefit for your effort. Gradually expand your implementation to build a comprehensive defense. Explore more tips in the Threat Intelligence article.
Integrating Security Audits into Compliance
Security audits play a crucial role in maintaining and verifying Essential 8 compliance. These systematic evaluations help identify security gaps, ensure controls are functioning correctly, and validate that your organization meets the required standards.
Types of Security Audits
Effective security audit programs typically include multiple approaches:
- Internal Audits: Conducted by your own security team to regularly assess compliance
- External Audits: Performed by third-party specialists who provide an objective assessment
- Automated Continuous Monitoring: Tools that constantly verify security controls
- Compliance Verification: Specific assessments against the Essential 8 requirements
Preparing for Security Audits
Successful audits require thorough preparation:
- Document all security policies and procedures
- Maintain up-to-date asset inventories
- Keep records of all security incidents and responses
- Track configuration changes and approvals
- Prepare evidence of control implementation
Conducting Effective Audits
Follow these steps for meaningful security audits:
- Establish Scope: Define which systems, applications, and controls will be assessed
- Gather Evidence: Collect documentation, run configuration checks, and interview personnel
- Analyze Findings: Identify compliance gaps and security weaknesses
- Develop Remediation Plans: Create actionable plans to address identified issues
- Verify Fixes: Confirm that remediation actions effectively resolve problems
Using Audit Results
Security audits provide valuable information for improving your security posture:
- Prioritize remediation based on risk levels
- Update security policies and procedures
- Refine implementation of Essential 8 controls
- Inform security awareness training programs
- Demonstrate compliance to stakeholders
Regular security audits create a feedback loop that strengthens your overall security posture. They help ensure that controls remain effective as your environment changes and as new threats emerge. For a deeper dive, consult this guide.
Vulnerability Management as a Core Component
Vulnerability management is the systematic process of identifying, assessing, and addressing security weaknesses in your systems and applications. This process forms a critical foundation for several Essential 8 controls, particularly patching applications and operating systems. The ACSC guide offers more details.
The Vulnerability Management Lifecycle
Effective vulnerability management involves four key phases:
- Identify: Discover vulnerabilities through automated scanning tools, penetration testing, and vendor advisories
- Classify and Prioritize: Evaluate discovered vulnerabilities based on severity, exploitability, and potential business impact
- Remediate: Address vulnerabilities by applying patches, configuration changes, or compensating controls
- Monitor: Maintain ongoing visibility through continuous scanning and security information/event management
Integration with Essential 8 Controls
Vulnerability management directly supports multiple Essential 8 strategies:
- Patch Applications: Reveals which apps need security updates
- Patch Operating Systems: Highlights OS-level weaknesses
- User Application Hardening: Identifies misconfigurations in browsers and other apps
- Restrict Administrative Privileges: Detects privilege escalation vulnerabilities
Implementing Vulnerability Management
To establish an effective vulnerability management program:
- Deploy scanning tools across your network
- Establish regular scanning schedules (weekly for critical systems)
- Adopt a risk-based approach to prioritize remediation
- Define service level agreements for addressing vulnerabilities
- Assign clear roles and responsibilities within the security team
- Document exceptions with appropriate approvals
Integrating vulnerability management ensures coverage of both known and emerging threats, creating a proactive security posture. Refer to the ACSC Assessment Process Guide for more best practices.
Achieving Structured Cybersecurity Compliance
Creating a structured cybersecurity compliance framework requires integrating Essential 8 guidelines with security audits and comprehensive vulnerability management. This combined approach builds a robust defense system that protects against existing threats while adapting to emerging risks.
Building a Layered Defense
A structured approach to cybersecurity creates multiple defensive layers:
- Preventive Controls: Whitelisting, privilege restriction, and macro settings
- Detective Controls: Vulnerability scanning, security monitoring, and audits
- Corrective Controls: Patching, configuration updates, and incident response
- Recovery Controls: Regular backups and tested restoration procedures
Business Benefits of Structured Compliance
Implementing a structured cybersecurity framework delivers substantial benefits:
- Reduced Risk Exposure by minimizing the attack surface
- Business Continuity through reliable backups and tested recovery plans
- Regulatory Alignment that meets or exceeds broader requirements
- Operational Efficiency via standardized security processes
- Competitive Advantage leading to greater customer trust
- Cost Reduction by preventing breaches and reducing remediation expenses
Case Study: Financial Services Implementation
A mid-sized financial services company adopted the Essential 8 framework after experiencing a ransomware attack. Their approach included:
- Application control and admin privilege restriction
- MFA for all remote access and privileged accounts
- Weekly vulnerability scanning and monthly patching cycles
- Quarterly security audits to verify control effectiveness
Results after 12 months:
- 85% reduction in security incidents
- Zero successful malware infections
- Shortened patch deployment time from weeks to days
- Improved regulatory compliance position
Case Study: Healthcare Provider
A regional healthcare provider implemented Essential 8 to protect sensitive patient data:
- Began with rigorous backups and restoration testing
- Deployed application whitelisting in clinical environments
- Implemented strict macro controls for administrative departments
- Established monthly vulnerability assessments and quarterly security audits
Results:
- Enhanced patient data protection
- Improved system availability in clinical areas
- Reduced security incidents by 70%
- Better alignment with healthcare data protection requirements
These examples illustrate how organizations can achieve powerful security improvements through a structured, phased approach to Essential 8 compliance implementation.
Conclusion
Essential 8 compliance implementation represents a fundamental building block for organizations seeking robust cybersecurity defenses. By systematically implementing these eight key strategies, businesses can significantly reduce their risk of cyber attacks.
The journey toward cybersecurity compliance is continuous rather than a destination. As threats evolve, so must your security controls and practices. Regular assessments, ongoing vulnerability management, and periodic security audits ensure your defenses remain effective.
Start with the most critical controls—application control, multi-factor authentication, backups, and patching—then gradually broaden to cover all areas. Even partial implementation of the Essential 8 offers substantial benefits. The key is to begin, prioritize high-impact steps, and expand as resources permit.
By committing to Essential 8 compliance, you build a security foundation that safeguards your organization’s future, preserves customer trust, and enables sustained growth in an ever-evolving digital world.
Additional Resources
Below are valuable resources and tools to support your Essential 8 compliance journey.
Official Documentation
- Australian Cyber Security Centre (ACSC) Essential Eight
- Essential Eight Maturity Model
- Essential Eight Assessment Process Guide
Implementation Tools
Application Control: Microsoft AppLocker, Carbon Black, Airlock Digital, Ivanti Application Control
Patching Solutions: Microsoft WSUS, IBM BigFix, Tanium, ManageEngine Patch Manager Plus
Multi-factor Authentication: Microsoft Authenticator, Duo Security, Okta, YubiKey
Backup Solutions: Veeam, Veritas NetBackup, Commvault, Acronis Cyber Backup
Vulnerability Management: Tenable Nessus, Qualys, Rapid7 InsightVM, OpenVAS
Additional Reading
- UpGuard on Essential 8
- Scytale Essential 8 Maturity Model Guide
- Threat Intelligence Blog: Essential 8 Implementation
- Zero Trust Guide to Essential 8 Compliance
- ACSC Assessment Process Guide
Consulting Services
If you need additional assistance with security audits or Essential 8 compliance:
- Explore cybersecurity consulting firms specializing in Australian standards
- Consider Managed Security Service Providers (MSSPs) offering Essential 8 assessments
- Check the ACSC website for certified security providers
Frequently Asked Questions
- Is Essential 8 mandatory for all businesses?
- Which control should I start with?
- How do security audits fit into Essential 8 compliance?
- Is partial implementation still valuable?
No. While strongly recommended across all sectors in Australia, it is only mandatory for certain government agencies and critical infrastructure providers. However, many private organizations adopt it voluntarily for added protection and customer confidence.
Focus first on high-impact controls such as multi-factor authentication, restricting administrative privileges, and patching. These measures provide significant risk reduction with relatively manageable implementation efforts.
Security audits ensure ongoing compliance by identifying gaps in your current controls. They offer insights into areas needing improvement and help maintain the effectiveness of your Essential 8 strategies.
Absolutely. Even implementing some of the Essential 8 controls can drastically reduce your organization’s attack surface. Prioritize the strategies most relevant to your highest risks and expand coverage over time.
